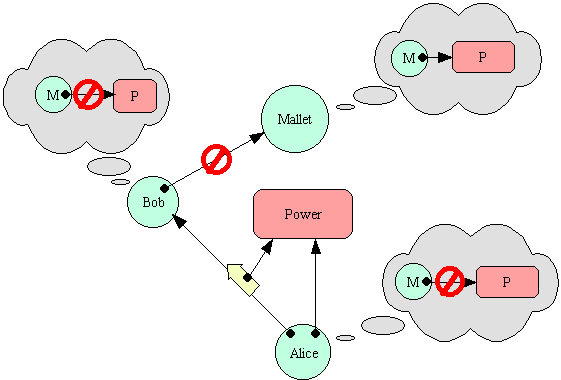

Alice gives Bob a power that she wishes Mallet not to have. Bob
and Mallet are not supposed to be in communication, and Bob does not wish
to give the power to Mallet. Can Mallet break in and take the power
anyway? Preventing this is the problem of Perimeter Security.
| Operating Systems | MMUs |
| Open Networks | Cryptography |
| Languages | Compilers
Interpreters Verifiers |
| Hardware | Tag bits
Bounds Checks etc... |
Impenetrable Shields
|
||
Sifting Garbage
|
||
Rubber Hose
|